- Rdp Cracking Tools V1.06 Rar Download
- Rdp Cracking Tools V1.06 Rar Extractor
- Rdp Cracking Tools V1.06 Rar File Opener
- Rdp Cracking Tools V1.06 Rar Gratuit
00 05 0day link exploit 100 100 fud OwnZ Crypter 20 2012 2014 2020 25 3xpl0iter 40 404 Crypter.404 Crypter download 404 Crypter download cracked 70 7d 888 888 RAT 1.0.9 Cracked 888 RAT 1.0.9 download 888 RAT 1.1.1 888 RAT 1.1.1 cracked 888 RAT Cracked 888 RAT Private - Cracked Account AccountReaper accounts accounts2 Activated admin Advanced.
TeamViewer 15 Crack is a popular desktop sharing and remote desktop software to access a PC or transfer files best computers. It remotely control computers and all the features of another computer from your PC. It empowers you to connect to a remote computer over the Internet and use it as though it were a local desktop. The app is an online video conferencing solution that connects any PC, mobile, Windows, Linux, Mac and server to each other globally. The solution TeamViewer is a simple and user-friendly interface with easy to use features.
- Remote Administration Tools. FREE AND HUGE PACK OF HACKING TOOLS OF 600 MB THAT YOU DONT GET ANYWHERE ELSE.
- CARDING TOOLS:) 1.HMAChekcer.rar 2. DigitalKeyloggerv3.3.rar 3. All in one checker.rar. 17.Ebay Cracker.rar 18.RDP Brute Cracked 19.Dorker – Dork Maker 20.Project Encypher.rar 21.Zenmate VPN Account Checker PM ON ICQ:@747606133, For the download links have em for sale and a lot more!
- A password cracking tool written in perl to perform a dictionary-based attack on a specific Facebook user through HTTPS. Morxbrute: 1.01: A customizable HTTP dictionary-based password cracking tool written in Perl. Morxbtcrack: 1.0: Single Bitcoin private key cracking tool released. Morxcoinpwn: 1.0.
TeamViewer 15 License Key is the best solution for remote control and file transfer from one PC to another. Users can connect to other PC just by running TeamViewer on both systems without the need for installation. With the first start, auto partner IDs are generated on both PC. Users can enter their partner’s ID into TeamViewer & the connection is connect quickly. Also, users can connect two computers from different locations.
Users can control the whole system freely. You can do all this without any issues. This is a very great application if users are at a distance. So, users can share the system authorizations & start work on it. It works behind any firewall & NAT proxy. This tool can help users when linking with the opposite system.
TeamViewer 15.12.10 Crack + License Key Latest Version
TeamViewer 15 Key can offer the convenience of being downloaded & installed on users’ PC, as well as access via the cloud, rendering it an easy-to-implement program. Mac/PC users alike will find TeamViewer’s remote capabilities to be secure.
Additionally, it is suitable for businesses of all sizes and can be extended both on the premise as well as the cloud. The program gives end-to-end encryption in addition to full support concerning mobile devices. TeamViewer 15 Keygen supports technical support, augmented reality, a billion devices. It enables users to access all the features of the PC.
TeamViewer 15 Portable Crack has impressive features like drag-and-drop/ file transfer/text chat/a whiteboard, session recording and also communicating between devices is simple. This remote desktop application has implemented high-security measures so that the user’s information will be secure.
TeamViewer for Mac free download with crack
TeamViewer for Mac Crack offers powerful features such as document management, invitation management, remote control and cooperative writing. Similarly, it also includes messaging, chat and screen sharing. Its instant messaging function covers features such as web-based chat, group chat and even customer-initiated chat. Moreover, it also supports offline messaging as well as chat history.
TeamViewer 15 Mac Crack is a powerful remote desktop tool to connect your Apple products. Users might also benefit from music in any way that users want. So, users can also get apple music with it. It is the best remote entry application in the world as compare to other someone.
Typically this tool uses cloud-based technologies to work together in real-time worldwide and authorize online support that features Blizz (online collaboration) and Monitis (website monitoring system) in addition to ITBrain (anti-malware) between others. TeamViewer for Mac gives more advancements to audio tracks in addition to video recording about remote sessions.
Furthermore, if the connection is fast enough, you can listen and view carefully to a similar thing that another user is seeing. Whether they are video demonstrations or other system functions. This thing made it easy for individuals to post their ideas or perhaps business demonstrations with colleagues who are not personally attending a meeting.
To sum up, TeamViewer 15 Portable can do almost all of the anticipations linked to the connection rate, which can be probably the essential concern. In short, it is used for meetings, presentations and provides a user with a new conference call from anywhere. You might also download other Desktop Remote Control Software from PiratesFile.
TeamViewer 15 Key Features
Highest Security Standard
- The program is very secure and easy to use.
- The business modifications emphasize completely secure data channels along with key exchange plus RC4 session development.
- Likewise, it also applies standard security through SSL and HTTPS.
No Installation Required
- There are no admin rights required for installing the software.
- Its offices are also located in the United States.
- TeamViewer Portable is for both small businesses and large businesses.
Interface
- This application’s interface is simple and easy to use.
- Users find no difficulties while using this tool.
- TeamViewer software is secure connected and supports teams for quick support.
High Performance
- It is optimized for connections over LANs as well as the Internet.
- TeamViewer 15 Activator includes an automatic bandwidth-based quality choice for optimized use on any connection.
File Transfer
- TeamViewer Key comes with combined file transfer that permits you to copy folders & also files.
- It is fast and secure solutions for remote access.
Works behind Firewalls
- Moreover, it will find a route to another computer because it works behind firewall.
Remote Control without Installation
- With TeamViewer, you can control a computer or smartphone remotely from anywhere at any time.
Remote Presentation of Products
- Moreover, Team Viewer Cracked lets you perform your desktop to a partner’s PC.
- With this app, you can show presentations and other stuff over the Internet within seconds; live from your system.
TeamViewer Alternative
- AnyDesk
TeamViewer 15 Activation Key
7G6F5-788BV-6V5B7-867B6-68YYT
I5D67-96C4X-5C6V7-BBC48-76GT6
76G85-46C6V-7B865-C769V-89J76
GUD9393-FGJD94I-GFOID93-GFOD93
DIOD94W-DFJKD0-DFKLD0-GJKD030
DFJKDI3-DFJKDI3-DFJKDIED
TeamViewer 15 Key
7G6F5-788BV-6V5B7-867B6-68YYT
I5D67-96C4X-5C6V7-BBC48-76GT6
DFJKDIE-DFJKDI-DFJKDIEJD
DI9E93U-FUD992U-E0292UW-RJIE92
76G85-46C6V-7B865-C769V-89J76
What is TeamViewer?
TeamViewer is a brilliant piece of the software program used for Internet-based remote access. The TeamViewer Download can link to any device or computer, so that you may remotely control your own partner’s PC. It enables you to distantly manage and access the PC associated with your computers plus servers from anyplace on a better internet connection.
TeamViewer quick support is for handheld remote control, web conferences, file transfer, online conference and desktop computer sharing. In short, it is a program that shares your own system screen (PC/Laptop/mobile) with some other person in-display mirroring.
What is the purpose of TeamViewer?
The purpose of this software is to access another PC remotely while you are sitting at any place. It lets you control and access all the features which other computers have.
How to use TeamViewer?
Using TeamViwer is easy and simple and you don’t have to be an expert for using this software. With the following step-by-step guide you’ll know how to use TeamViewer properly.
How does Teamviewer work step-by-step
- First of all, click on the TeamViewer icon.
- Now, sometimes an “unattended setup” wizard appears on the screen; simply click Cancel.
- If you are new, click on Try it now at the top right of the popup window. It will make sure that your dashboard is up-to-date.
- Open the TeamViewer on another PC to which you want to connect or remotely control.
- In the next step, now review the 2nd PC’s Password and ID.
- Put the second PC’s ID into the “Partner ID” tab on the first computer you want to connect.
- Click on the Connect button to proceed.
- Now enter the 2nd computer’s Password and click on log on.
- Once it’s done, now you’re connected to another PC and can control it from your desktop. Enjoy!
How to connect TeamViewer?
TeamViewer is simple and easy to use remote control desktop software that requires two computers or laptop to connect.
- Download the remote desktop application from below.
- Install the software.
- Select one of the personal use option or company use options and configure the process.
- Create an account with email and password.
- Activate your TeamViewer account via your email inbox.
- Create a new account on another device (which you want to connect with).
- Note the ID number and paste it onto another device (or share this ID number with your friend to connect). Then enter your password.
- Now you can use another device remotely and also can transfer a file or do the presentation.
How much does TeamViewer cost?
It costs almost $49/month which is nearly $588 per year. But don’t worry, you can get the remote desktop software for free from the link below.
How to update TeamViewer?
- Open the software.
- Click on Extras at the top right corner & click on the option.
- Now a new wizard will appear on the screen click on the advanced option. At the end, simply click on “all updates” and press OK to proceed. All done!
How to install TeamViewer on Mac?
- Download TeamViewer Mac Crack from https://piratesfile.com/
- Click the downloaded TeamViewer.dmg file to proceed further.
- Install the software and complete the process.
- Done
How to uninstall TeamViewer?
To uninstall TeamViewer,
- Press and hold Windows icon + Q
- Type Control Panel.
- Select Program> Uninstall a Program.
- Search TeamViewer.
- Click on uninstall.
- Select Yes.
Pros
- Completely free to use
- Supports chat (text, video, and voice over IP)
- No port forwarding configurations are necessary
- Spontaneous support
- Works with multiple monitors
- Can start and join meetings
- Remote printing is allowed
- Supports Wake-on-LAN (WOL)
Cons
- ID number might change unexpectedly
- Users can’t use it for free in commercial settings
TeamViewer 15 System Requirements
Operating System
- Microsoft Windows XP, Vista, 7, 8, 8.1, Windows 10 and Linus as well as macOS
RAM Memory
- 2 GB of RAM at least
Processor
- Support 1 GHz processor
Hard Drive
- Require 240 MB of free hard disk space
Internet
- Internet connection required for many purposes

How Install TeamViewer?
- At first, you may uninstall the earlier version with IObit Uninstaller Pro.
- After that, download the Team Viewer Full Version with IDM.
- Turn off Windows defender
- Then, extract the downloaded file with the help of WinRAR
- Afterwards, install the software.
- After installation do not run it.
- Copy the crack files and paste them to the installation folder.
- In the end, restart your PC.
- Done!
Important Note! Please make sure not to update/upgrade the TeamViewer Portable; otherwise, the program will not work forever. Thanks!
You Can Download TeamViewer 15 Crack + Activation Key From The Link Below…
You might also like old version
Passwords are the most commonly used method for user authentication. Passwords are so popular because the logic behind them makes sense to people and they’re relatively easy for developers to implement.
However, passwords can also introduce security vulnerabilities. Password crackers are designed to take credential data stolen in a data breach or other hack and extract passwords from it.
What is password cracking?
A well-designed password-based authentication system doesn’t store a user’s actual password. This would make it far too easy for a hacker or a malicious insider to gain access to all of the user accounts on the system.
Instead, authentication systems store a password hash, which is the result of sending the password — and a random value called a salt — through a hash function. Hash functions are designed to be one-way, meaning that it is very difficult to determine the input that produces a given output. Since hash functions are also deterministic (meaning that the same input produces the same output), comparing two password hashes (the stored one and the hash of the password provided by a user) is almost as good as comparing the real passwords.
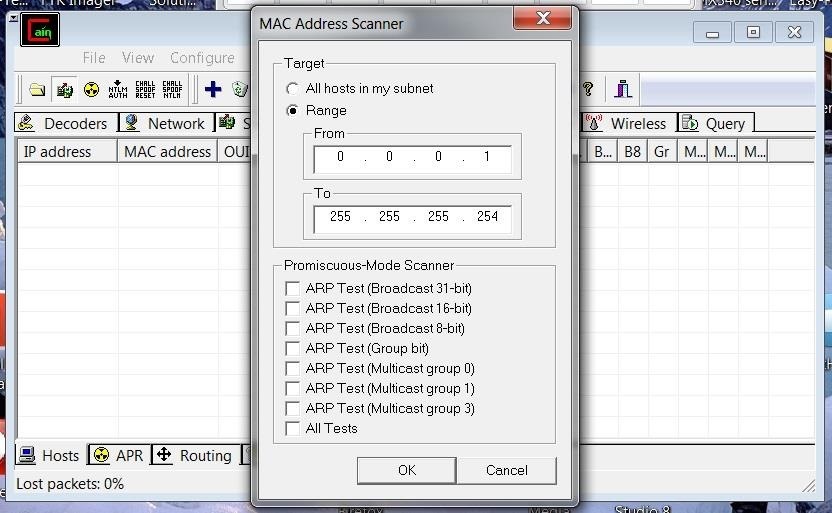
Password cracking refers to the process of extracting passwords from the associated password hash. This can be accomplished in a few different ways:
- Dictionary attack: Most people use weak and common passwords. Taking a list of words and adding a few permutations — like substituting $ for s — enables a password cracker to learn a lot of passwords very quickly.
- Brute-force guessing attack: There are only so many potential passwords of a given length. While slow, a brute-force attack (trying all possible password combinations) guarantees that an attacker will crack the password eventually.
- Hybrid attack: A hybrid attack mixes these two techniques. It starts by checking to see if a password can be cracked using a dictionary attack, then moves on to a brute-force attack if it is unsuccessful.
Most password-cracking or password finder tools enable a hacker to perform any of these types of attacks. This post describes some of the most commonly used password-cracking tools.
1. Hashcat
Hashcat is one of the most popular and widely used password crackers in existence. It is available on every operating system and supports over 300 different types of hashes.
Hashcat enables highly-parallelized password cracking with the ability to crack multiple different passwords on multiple different devices at the same time and the ability to support a distributed hash-cracking system via overlays. Cracking is optimized with integrated performance tuning and temperature monitoring.
Download Hashcat here.
2. John the Ripper
John the Ripper is a well-known free open-source password cracking tool for Linux, Unix and Mac OS X. A Windows version is also available.
John the Ripper offers password cracking for a variety of different password types. It goes beyond OS passwords to include common web apps (like WordPress), compressed archives, document files (Microsoft Office files, PDFs and so on), and more.
A pro version of the tool is also available, which offers better features and native packages for target operating systems. You can also download Openwall GNU/*/Linux that comes with John the Ripper.
Download John the Ripper here.
3. Brutus
Brutus is one of the most popular remote online password-cracking tools. It claims to be the fastest and most flexible password cracking tool. This tool is free and is only available for Windows systems. It was released back in October 2000.
Brutus supports a number of different authentication types, including:
- HTTP (basic authentication)
- HTTP (HTML Form/CGI)
- POP3
- FTP
- SMB
- Telnet
- IMAP
- NNTP
- NetBus
- Custom protocols
It is also capable of supporting multi-stage authentication protocols and can attack up to sixty different targets in parallel. It also offers the ability to pause, resume and import an attack.
Brutus has not been updated for several years. However, its support for a wide variety of authentication protocols and ability to add custom modules make it a popular tool for online password cracking attacks.
Get the Brutus password finder online here.
4. Wfuzz
Wfuzz is a web application password-cracking tool like Brutus that tries to crack passwords via a brute-force guessing attack. It can also be used to find hidden resources like directories, servlets and scripts. Wfuzz can also identify injection vulnerabilities within an application such as SQL injection, XSS injection and LDAP injection.
Key features of the Wfuzz password-cracking tool include:
- Injection at multiple points in multiple directories
- Output in colored HTML
- Post, headers and authentication data brute-forcing
- Proxy and SOCK support, multiple proxy support
- Multi-threading
- HTTP password brute-force via GET or POST requests
- Time delay between requests
- Cookie fuzzing
5. THC Hydra
THC Hydra is an online password-cracking tool that attempts to determine user credentials via brute-force password guessing attack. It is available for Windows, Linux, Free BSD, Solaris and OS X.
THC Hydra is extensible with the ability to easily install new modules. It also supports a number of network protocols, including Asterisk, AFP, Cisco AAA, Cisco auth, Cisco enable, CVS, Firebird, FTP, HTTP-FORM-GET, HTTP-FORM-POST, HTTP-GET, HTTP-HEAD, HTTP-PROXY, HTTPS-FORM-GET, HTTPS-FORM-POST, HTTPS-GET, HTTPS-HEAD, HTTP-Proxy, ICQ, IMAP, IRC, LDAP, MS-SQL, MYSQL, NCP, NNTP, Oracle Listener, Oracle SID, Oracle, PC-Anywhere, PCNFS, POP3, POSTGRES, RDP, Rexec, Rlogin, Rsh, SAP/R3, SIP, SMB, SMTP, SMTP Enum, SNMP, SOCKS5, SSH (v1 and v2), Subversion, Teamspeak (TS2), Telnet, VMware-Auth, VNC and XMPP.
Download THC Hydra here.
If you are a developer, you can also contribute to the tool’s development.
6. Medusa
Medusa is an online password-cracking tool similar to THC Hydra. It claims to be a speedy parallel, modular and login brute-forcing tool. It supports HTTP, FTP, CVS, AFP, IMAP, MS SQL, MYSQL, NCP, NNTP, POP3, PostgreSQL, pcAnywhere, rlogin, SMB, rsh, SMTP, SNMP, SSH, SVN, VNC, VmAuthd and Telnet.
Medusa is a command-line tool, so some level of command-line knowledge is necessary to use it. Password-cracking speed depends on network connectivity. On a local system, it can test 2,000 passwords per minute.
Medusa also supports parallelized attacks. In addition to a wordlist of passwords to try, it is also possible to define a list of usernames or email addresses to test during an attack.
Read more about this here.
Download Medusa here.
7. RainbowCrack
All password-cracking is subject to a time-memory tradeoff. If an attacker has precomputed a table of password/hash pairs and stored them as a “rainbow table,” then the password-cracking process is simplified to a table lookup. This threat is why passwords are now salted: adding a unique, random value to every password before hashing it means that the number of rainbow tables required is much larger.
RainbowCrack is a password cracking tool designed to work using rainbow tables. It is possible to generate custom rainbow tables or take advantage of preexisting ones downloaded from the internet. RainbowCrack offers free downloads of rainbow tables for the LANMAN, NTLM, MD5 and SHA1 password systems.
Download rainbow tables here.
A few paid rainbow tables are also available, which you can buy from here.
This tool is available for both Windows and Linux systems.
Download RainbowCrack here.
8. OphCrack
Rdp Cracking Tools V1.06 Rar Download
OphCrack is a free rainbow table-based password cracking tool for Windows. It is the most popular Windows password cracking tool but can also be used on Linux and Mac systems. It cracks LM and NTLM hashes. For cracking Windows XP, Vista and Windows 7, free rainbow tables are also available.
A live CD of OphCrack is also available to simplify the cracking. One can use the Live CD of OphCrack to crack Windows-based passwords. This tool is available for free.
Download OphCrack here.
Download free and premium rainbow tables for OphCrack here.
9. L0phtCrack
L0phtCrack is an alternative to OphCrack. It attempts to crack Windows passwords from hashes. For cracking passwords, it uses Windows workstations, network servers, primary domain controllers and Active Directory. It also uses dictionary and brute-force attacks for generating and guessing passwords. It was acquired by Symantec and discontinued in 2006. Later, L0pht developers again reacquired it and launched L0phtCrack in 2009.
L0phtCrack also comes with the ability to scan routine password security scans. One can set daily, weekly or monthly audits, and it will start scanning at the scheduled time.
Learn about L0phtCrack here.
10. Aircrack-ng
Aircrack-ng is a Wi-Fi password-cracking tool that can crack WEP or WPA/WPA2 PSK passwords. It analyzes wireless encrypted packets and then tries to crack passwords via the dictionary attacks and the PTW, FMS and other cracking algorithms. It is available for Linux and Windows systems. A live CD of Aircrack is also available.
Aircrack-ng tutorials are available here.
Download Aircrack-ng here.
How to create a password that’s hard to crack
In this post, we have listed 10 password-cracking tools. These tools try to crack passwords with different password-cracking algorithms. Most of the password cracking tools are available for free. So, you should always try to have a strong password that is hard to crack. These are a few tips you can try while creating a password.
- The longer the password, the harder it is to crack: Password length is the most important factor. The complexity of a brute force password guessing attack grows exponentially with the length of the password. A random seven-character password can be cracked in minutes, while a ten-character one takes hundreds of years.
- Always use a combination of characters, numbers and special characters: Using a variety of characters also makes brute-force password-guessing more difficult, since it means that crackers need to try a wider variety of options for each character of the password. Incorporate numbers and special characters and not just at the end of the password or as a letter substitution (like @ for a).
- Variety in passwords: Credential stuffing attacks use bots to test if passwords stolen from one online account are also used for other accounts. A data breach at a tiny company could compromise a bank account if the same credentials are used. Use a long, random, and unique password for all online accounts.
What to avoid while selecting your password
Rdp Cracking Tools V1.06 Rar Extractor
Cybercriminals and password cracker developers know all of the “clever” tricks that people use to create their passwords. A few common password mistakes that should be avoided include:
- Using a dictionary word: Dictionary attacks are designed to test every word in the dictionary (and common permutations) in seconds.
- Using personal information: A pet’s name, relative’s name, birthplace, favorite sport and so on are all dictionary words. Even if they weren’t, tools exist to grab this information from social media and build a wordlist from it for an attack.
- Using patterns: Passwords like 1111111, 12345678, qwerty and asdfgh are some of the most commonly used ones in existence. They’re also included in every password cracker’s wordlist.
- Using character substitutions: Character substitutions like 4 for A and $ for S are well-known. Dictionary attacks test for these substitutions automatically.
- Using numbers and special characters only at the end: Most people put their required numbers and special characters at the end of the password. These patterns are built into password crackers.
- Using common passwords: Every year, companies like Splashdata publish lists of the most commonly used passwords. They create these lists by cracking breached passwords, just like an attacker would. Never use the passwords on these lists or anything like them.
- Using anything but a random password: Passwords should be long, random, and unique. Use a password manager to securely generate and store passwords for online accounts.
Rdp Cracking Tools V1.06 Rar File Opener
Conclusion
Password-cracking tools are designed to take the password hashes leaked during a data breach or stolen using an attack and extract the original passwords from them. They accomplish this by taking advantage of the use of weak passwords or by trying every potential password of a given length.
Rdp Cracking Tools V1.06 Rar Gratuit
Password finders can be used for a variety of different purposes, not all of them bad. While they’re commonly used by cybercriminals, security teams can also use them to audit the strength of their users’ passwords and assess the risk of weak passwords to the organization.